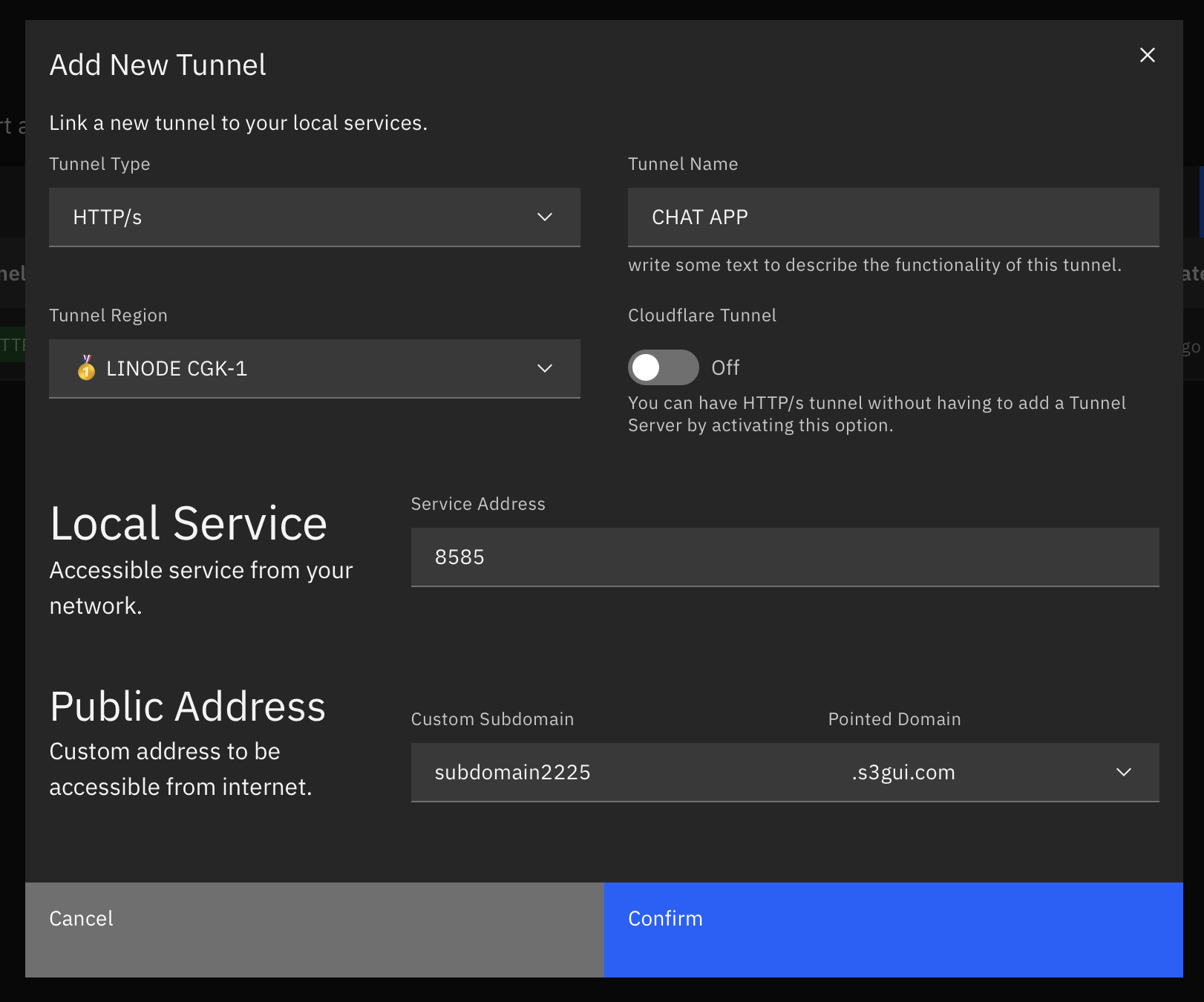
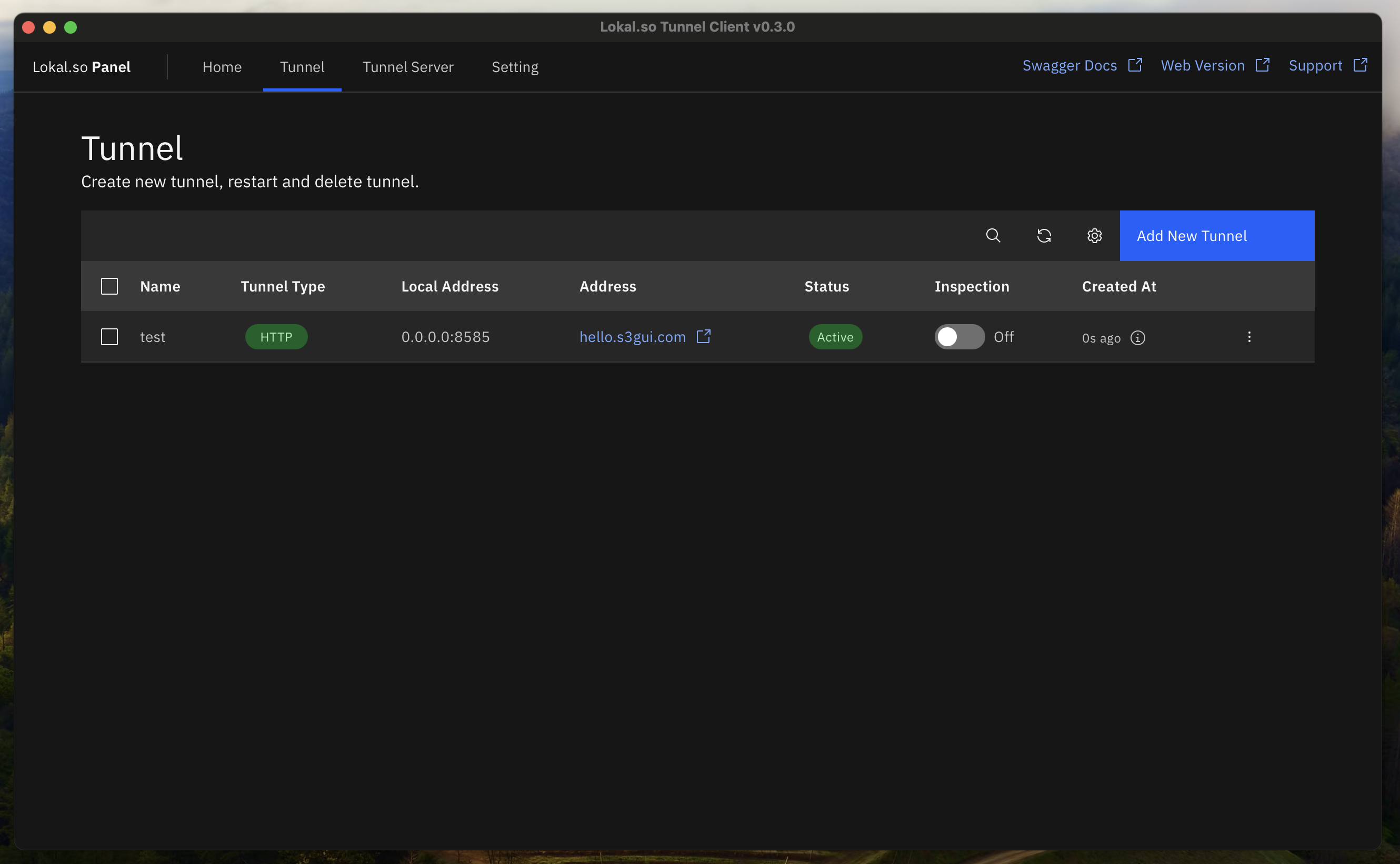
Enable HTTPS on Pointed Domain
Cloudflare DNS Manager
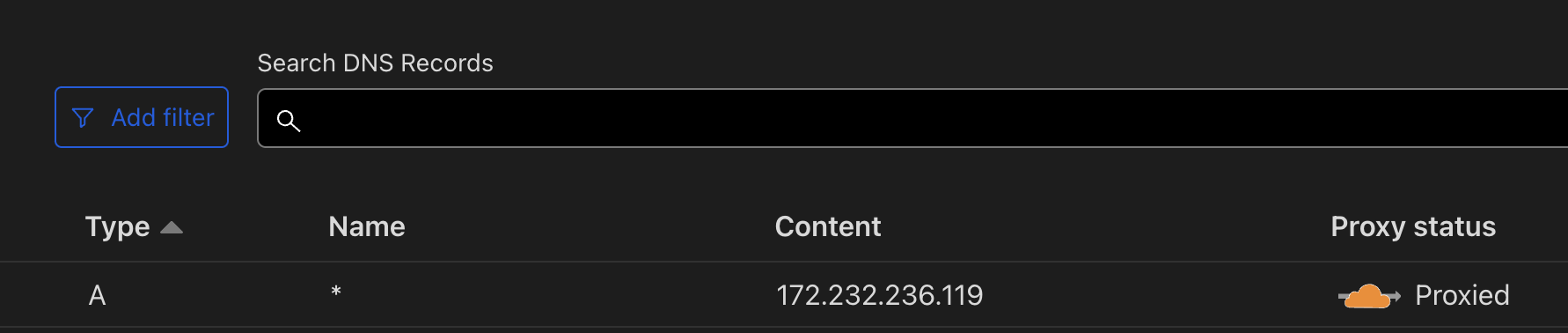
If you are already using Cloudflare DNS Manager, you could point your domain to the Tunnel’s VHOST_HTTP_HOST and use Wilcard * as the Name/Subdomain.
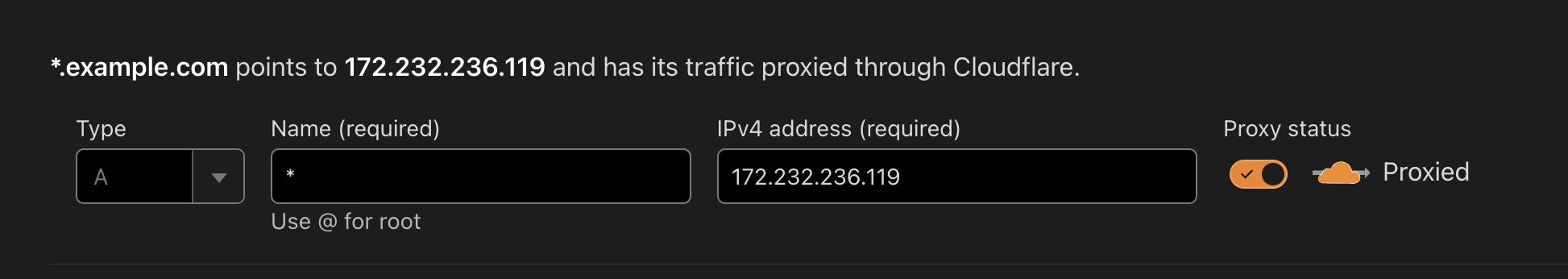
Using NGINX with Certbot
While you might be want to be more flexible with DNS Manager, this option may suit you the most,
before following the guide, make sure you had cerbot CLI installed, if you don’t have one,
please follow the Official Guide to install certbot CLI.
After you had certbot installed on your system, Let’s Encrypt require you to do some validation before you able to request for an SSL Certificate
and the most less error-prone way are using DNS as the validation challenges
for example, I had domain called s3gui.com
certbot certonly --manual --preferred-challenges dns -d "*.s3gui.com"here’s the full log of the process:
Saving debug log to /var/log/letsencrypt/letsencrypt.logRequesting a certificate for *.s3gui.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -Please deploy a DNS TXT record under the name:
_acme-challenge.s3gui.com.
with the following value:
thh5VFGiZHyNp8PcJR1_ojuyrL6tvgWVWAlYLRaHIMo
Before continuing, verify the TXT record has been deployed. Depending on the DNSprovider, this may take some time, from a few seconds to multiple minutes. You cancheck if it has finished deploying with aid of online tools, such as the GoogleAdmin Toolbox: https://toolbox.googleapps.com/apps/dig/#TXT/_acme-challenge.s3gui.com.Look for one or more bolded line(s) below the line ';ANSWER'. It should show thevalue(s) you've just added.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -Press Enter to Continue
Successfully received certificate.Certificate is saved at: /etc/letsencrypt/live/s3gui.com/fullchain.pemKey is saved at: /etc/letsencrypt/live/s3gui.com/privkey.pemThis certificate expires on 2024-10-15.These files will be updated when the certificate renews.
NEXT STEPS:- This certificate will not be renewed automatically. Autorenewal of --manual certificates requires the use of an authentication hook script (--manual-auth-hook) but one was not provided. To renew this certificate, repeat this same certbot command before the certificate's expiry date.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -If you like Certbot, please consider supporting our work by: * Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate * Donating to EFF: https://eff.org/donate-le- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -now, after you had this two files:
Certificate is saved at: /etc/letsencrypt/live/s3gui.com/fullchain.pemKey is saved at: /etc/letsencrypt/live/s3gui.com/privkey.pemyou may now update your nginx’s configuration file
server { listen 443 ssl; # Listen on port 443 with SSL
ssl_certificate /etc/letsencrypt/live/s3gui.com/fullchain.pem; ssl_certificate_key /etc/letsencrypt/live/s3gui.com/privkey.pem;
# Server name should match your wildcard domain
server_name *.s3gui.com;
# Optional: Enable HTTP Strict Transport Security (HSTS) to force HTTPS # add_header Strict-Transport-Security "max-age=31536000; includeSubDomains; preload"; # Rest of your server block configuration
location / { proxy_redirect off; proxy_pass http://127.0.0.1:80; # Proxy requests to your origin server proxy_set_header Host $host; proxy_http_version 1.1; proxy_set_header Upgrade $http_upgrade; proxy_set_header Connection "Upgrade"; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; }}If you wish your domain to be only receive HTTPS request, you might want to change Lokal’s VHOST_HTTP_PORT to be something else rather than using port 80
now after everything is being set-up, you might want to add the domain to Lokal Client
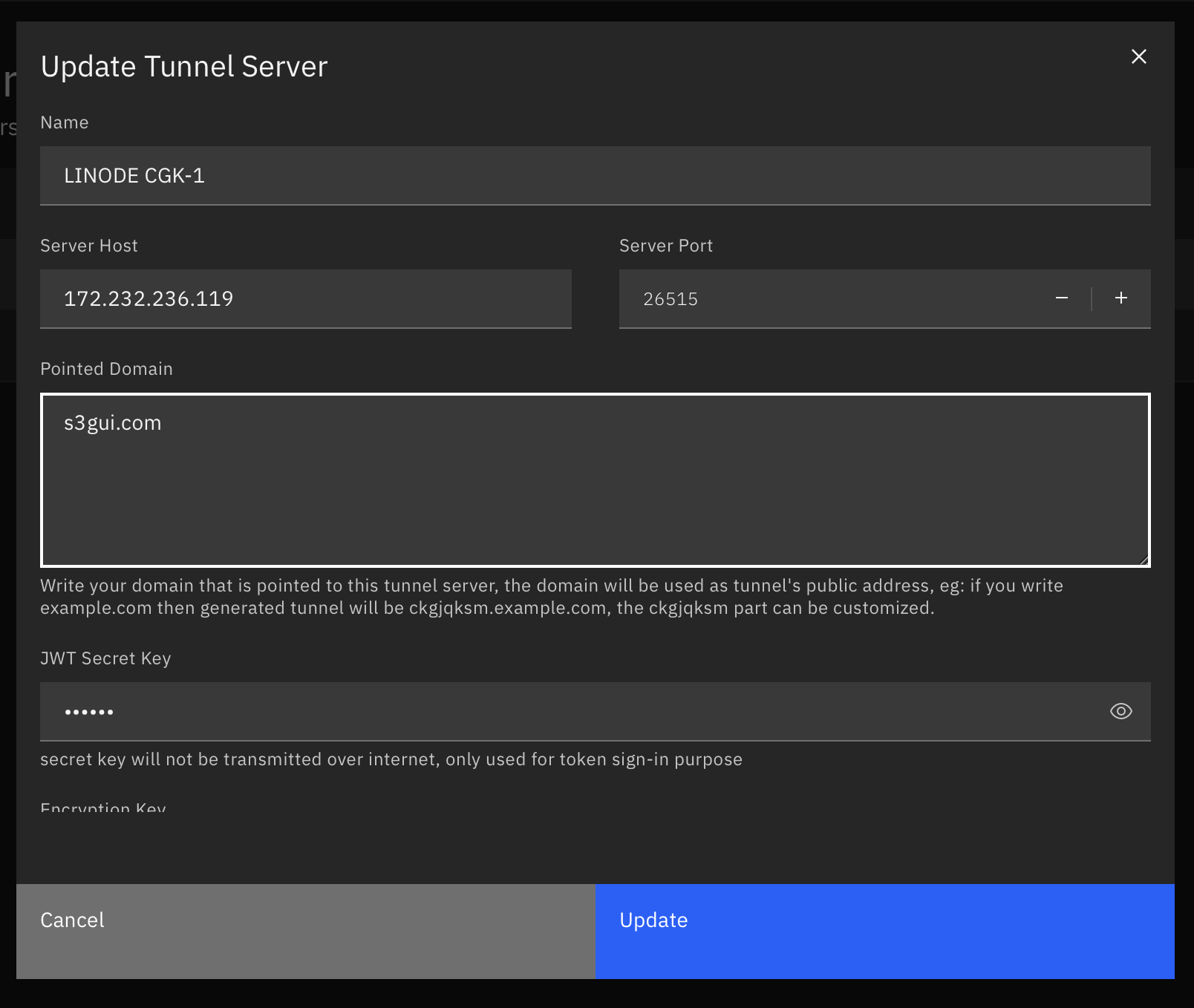
and now your HTTPS Domain are ready to use!